With the Linux VDA set to drop very shortly as part of the XenApp & XenDesktop 7.6 FP2 release. It seems like a good time to share the high level, yet detailed, set-up process I followed when successfully carrying out internal testing. Taken from various sources including the tech preview RHEL install guide, my colleague Lee Bushen’s detailed SLED based lab set-up guide and a tonne of Google searches and read-through’s, I hope this collection of posts can save people some time and be used and referenced as one of the definitive Linux VDA setup guides for CentOS 6.6.
With the Linux VDA set to drop very shortly as part of the XenApp & XenDesktop 7.6 FP2 release. It seems like a good time to share the high level, yet detailed, set-up process I followed when successfully carrying out internal testing. Taken from various sources including the tech preview RHEL install guide, my colleague Lee Bushen’s detailed SLED based lab set-up guide and a tonne of Google searches and read-through’s, I hope this collection of posts can save people some time and be used and referenced as one of the definitive Linux VDA setup guides for CentOS 6.6.
Although only officially supported on specific SUSE & Red Hat Enterprise Linux Distributions, CentOS 6.6 can also be used for reproduction and testing purposes due to its close code match to Red Hat, with the added bonus that it is easily accessible & free.
So, here it is, Part 1 of my step-by-step guide to help Windows aficionados & Linux newbies (myself included!) get the Linux VDA up and running on CentOS 6.6 without too much bother, for reference and testing purposes. Enjoy and sound off in the comments if you have any questions. :-)
Pt. 1 Installing and preparing the Linux OS
1. Download and install CentOS 6.6 distribution using the following links:
http://wiki.centos.org/Download
http://isoredirect.centos.org/centos/6/isos/x86_64/
2. Install CentOS 6.6 distribution (Physical or Virtual):
For the purposes of this guide I installed CentOS 6.6 as a virtual machine using the built-in CentOS 6 (64-bit) template with default values on XenServer 6.5 SP1
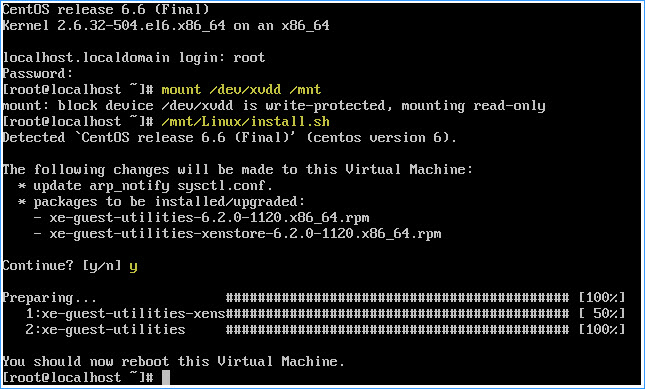
3. Install XenTools:
– Select VM menu –> Install XenServer Tools
– Paste or type mount /dev/xvdd /mnt into the VM console window and hit return
– Paste or type /mnt/Linux/install.sh into the VM console window and hit return
– Type y and hit return to continue
– Type reboot and hit return to reboot the CentOS 6.6 VM
4. Configure specific networking requirements
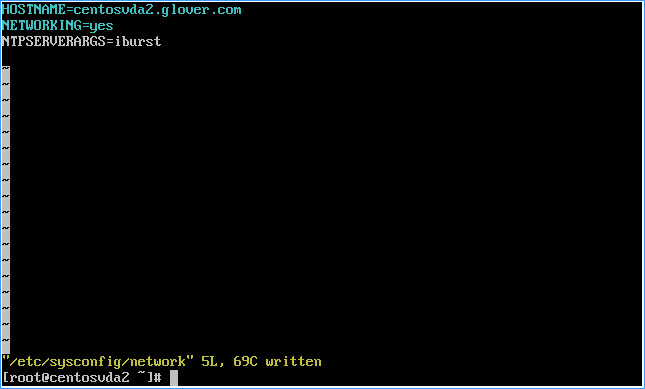
Set the hostname to one of your choosing (hostname will default to localhost):
Example hostname: centosvda2
– Type hostname centosvda2 at the VM console and hit return
– Paste or type vi /etc/sysconfig/network into the VM console window and hit return
– Press Shift + a to enter edit mode
– Set the values as such, replacing hostname to the name of your choosing:
HOSTNAME=centosvda2.glover.com
NETWORKING=yes
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file
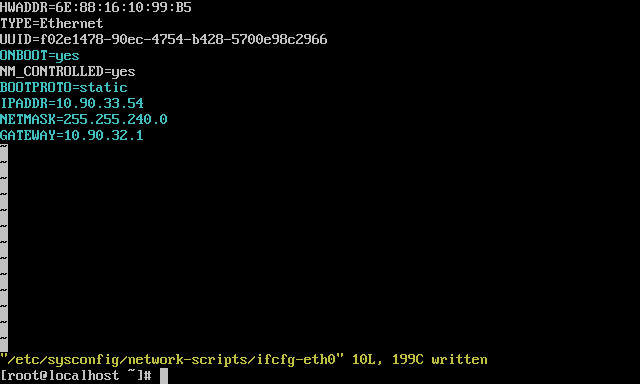
Set a Static IP by editing the required network config file as follows using network 0 (zero) as an example:
– Paste or type vi /etc/sysconfig/network-scripts/ifcfg-eth0 into the VM console window and hit return
– Press Shift + a to enter edit mode
– Set the values as such replacing the IP address details to match your own environment:
ONBOOT=yes
BOOTPROTO=Static
IPADDR=10.90.33.54
NETMASK=255.255.240.0
GATEWAY=10.90.32.1
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file:
Note: If you wish to assign IP details dynamically using DHCP then set the following values:
ONBOOT=yes
BOOTPROTO=Dynamic
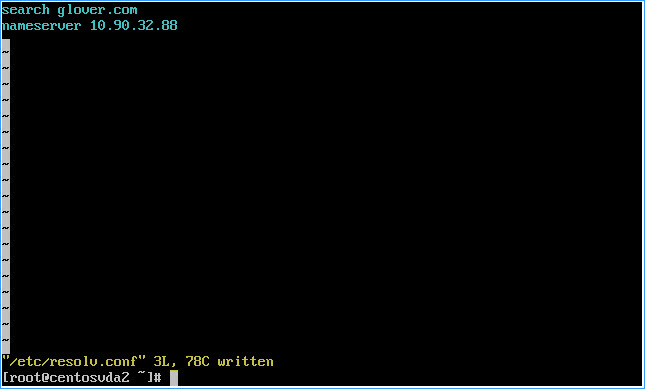
Add DNS support allowing dynamic name resolution by editing the resolv.conf file and adding all required nameservers as follows:
– Paste or type vi /etc/resolv.conf into the VM console window and hit return
– Press Shift + a to enter edit mode
– Set the values as such replacing the Domain and nameserver details to match your own environment
search glover.com
nameserver 10.90.32.88
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file
Protect the /etc/resolv.conf from being modified on reboot by setting the write-protection attribute as follows:
chattr +i /etc/resolv.conf
Assign loopback address to hostname & validate hostname:
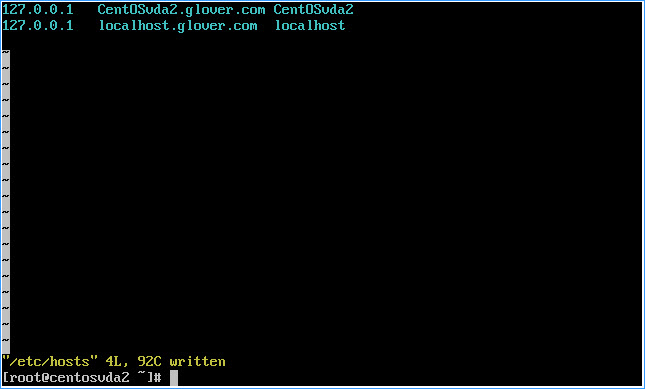
– Paste or type vi /etc/hosts and set as follows replacing details to match your own environment
– Press Shift + a to enter edit mode
– Set the values as such replacing the FQDN and hostname of the CentOS 6.6 VM to match your own environment:
127.0.0.1 CentOSvda2.glover.com CentOSvda2
127.0.0.1 localhost.glover.com localhost
Note: The 2nd localhost entry is required for the postgresql service to start successfully (covered in Pt.2 of the blog series…)
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file
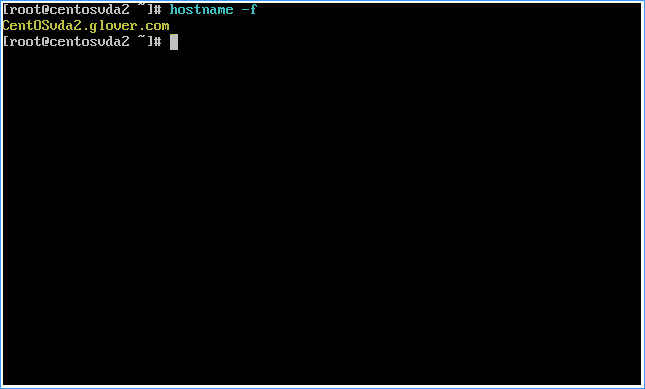
– Type hostname -f to validate that the hostname is set correctly
Note: This should return the machine’s fully qualified domain name (FQDN):
– Type reboot and hit return to reboot the CentOS 6.6 VM
5. Install rpm packages:
Paste the following into the VM console and hit return to install the relevant packages:
yum -y groupinstall “Desktop” “Desktop Platform” “X Window System” “Fonts”
yum -y install authconfig krb5-workstation pam_krb5 samba-common oddjob-mkhomedir
Note: If you receive the following error: PYCURL ERROR 22 – “The requested URL returned error: 404”
Run yum clean all and try again
6. Install and Configure xRDP to access the GUI remotely:
Install EPEL repository
– Paste rpm -Uvh http://download.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm into the VM console and hit return
Install xrdp package
– Paste yum -y install xrdp tigervnc-server into the VM console and hit return
Configure xrdp service
– Once installed, run service xrdp start to start the xrdp service
– Run chkconfig xrdp on to ensure xrdp service starts on boot
Note: If you receive an error when running “service xrdp start“, type reboot and hit return to reboot the CentOS 6.6 VM
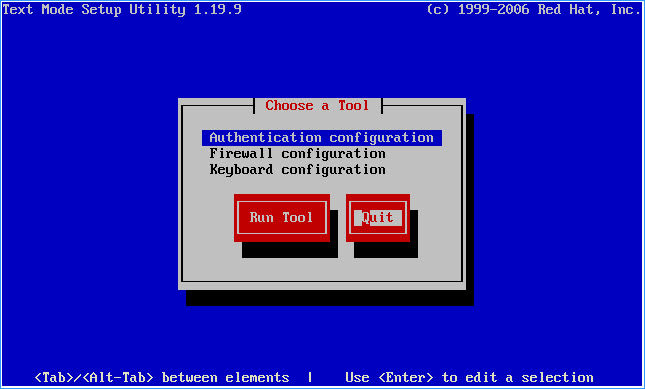
Select Quit to close the Text Mode Setup Utility:
7. Disable Firewall temporarily to allow remote access
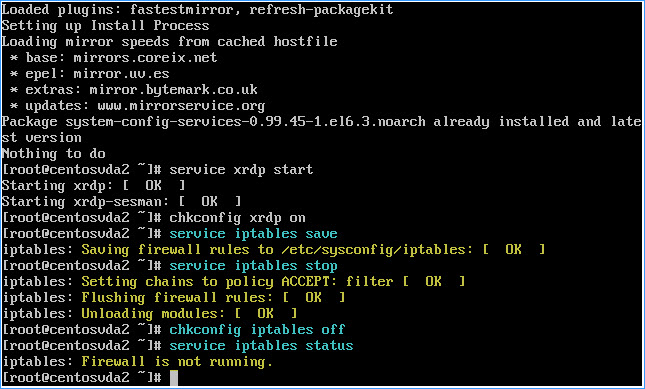
Issue the following commands in turn:
– service iptables save
– service iptables stop
– chkconfig iptables off
– service iptables status
Note: Once configuration of the CentOS VM is complete including the install and config or the Linux VDA itself, you should consider re-enabling the Firewall. It is also understood that the majority of people reading this blog series will be initially installing the Linux VDA in a purely test environment and will be well aware of the dangers associated with disabling the Firewall on a permanent basis. To re-enable the Firewall post configuration, issue the following commands in turn:
– service iptables save
– service iptables start
– chkconfig iptables on
– service iptables status
8. Configure NTP Service
Connect to the CentOS 6.6 VM using xRDP and the standard windows RDP client or Remote Desktop Manager Application and configure the Date and Time properties as follows:
Note: Click close to ignore the following warning if using the root user account to connect remotely:
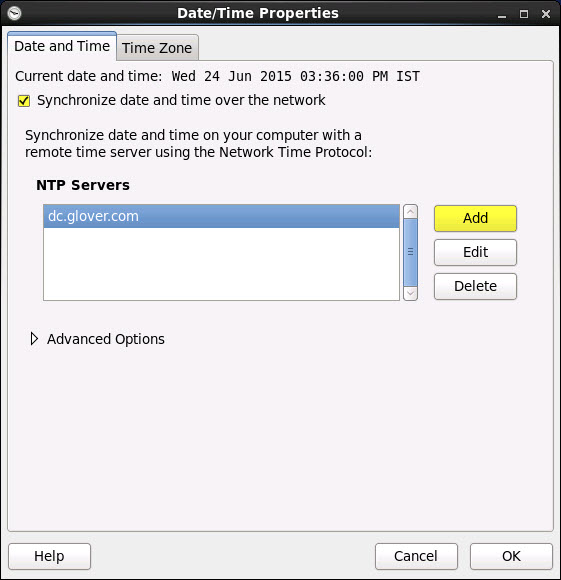
- Open the System menu > Administration > Date & Time
2. In the Date and Time tab, ensure Synchronize date and time over the network is checked
3. In the NTP Servers list, click Add
4. Enter the hostname or IP address of a local NTP Server and hit return. This is typically the hostname of the AD Domain Controller. The configuration tool will test for service reachability
5. Delete the other default NTP servers listed
6. Click OK. This will restart the NTP daemon
9. Join machine (CentOS 6.6 VM) to Domain
While connected to the CentOS VM over xRDP, click on the Applications menu > System Tools > Terminal
Paste or type authconfig-tui into the terminal window and hit return to bring up the GUI version of Autoconfig…
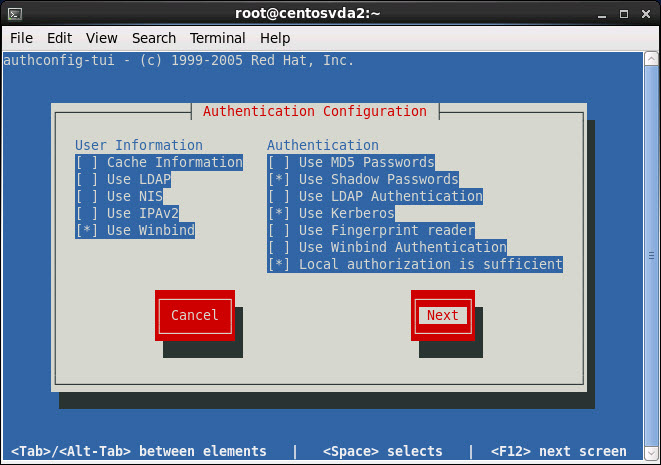
Configure as follows before clicking Next:
User Information:
-Use Winbind
Authentication:
-Use Shadow Passwords
-Use Kerberos
-Local authorization is enough
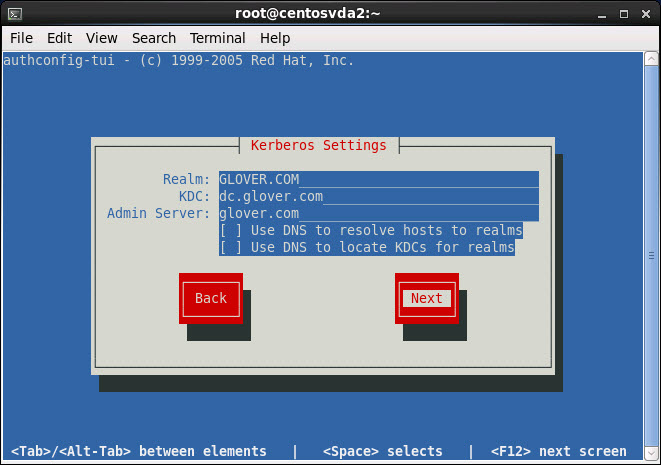
Set Kerberos settings as follows replacing the Realm, KDC and Admin Server values with those matching your own environment and click Next:
Realm: GLOVER.COM (Must be in caps)
KDC: dc.glover.com
Admin Server: glover.com
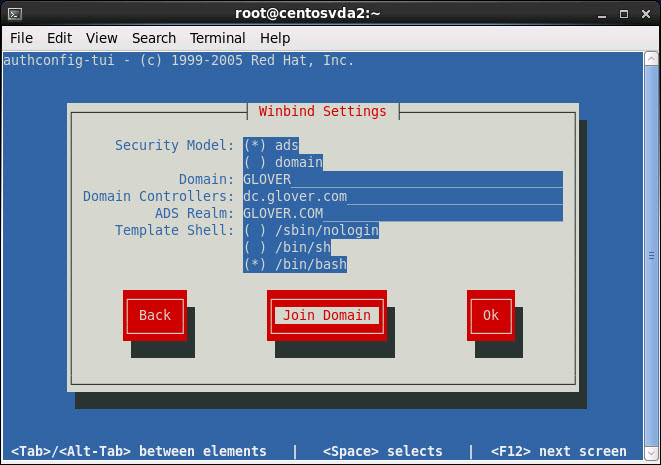
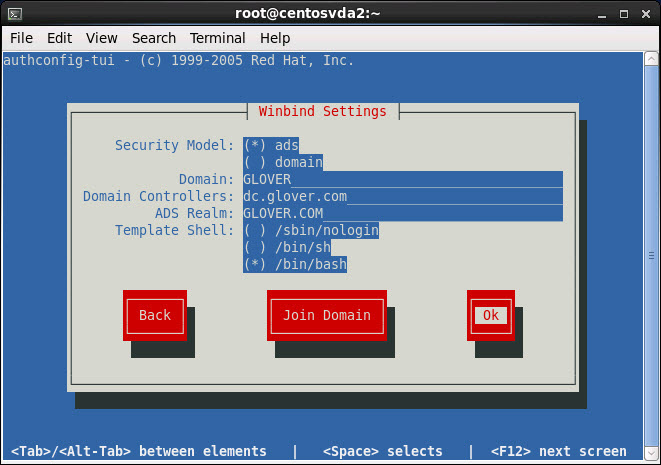
Set the Winbind settings as follows replacing the values with those that match your own environment and click Join Domain:
Security Model: ads
Domain: GLOVER
Domain Controllers: dc.glover.com
ADS Realm: GLOVER.COM (Caps required)
Template Shell: /bin/bash
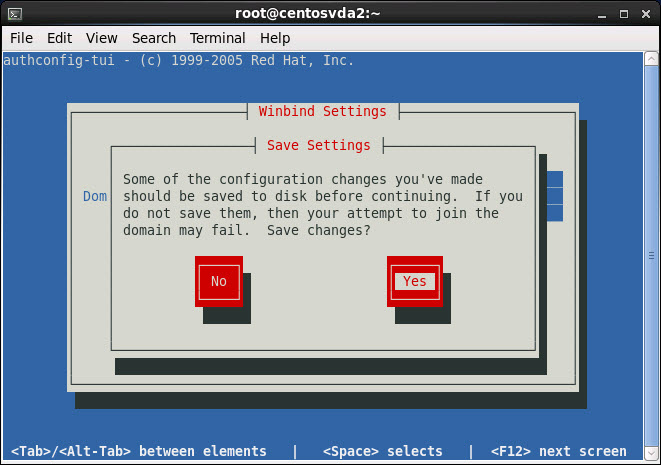
Select Yes to save configuration changes when prompted:
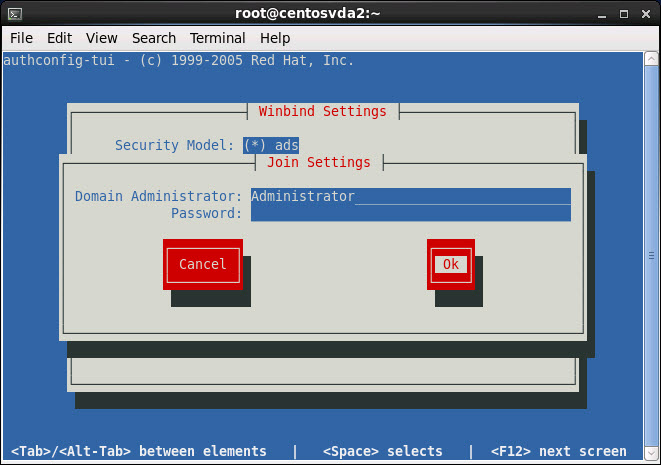
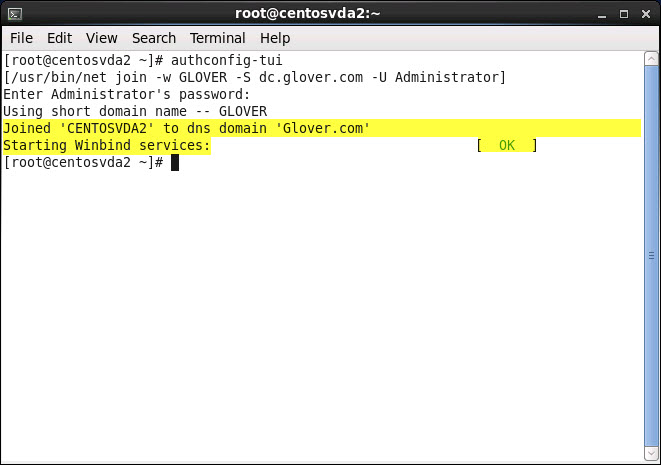
Type the Domain administrator password and select OK:
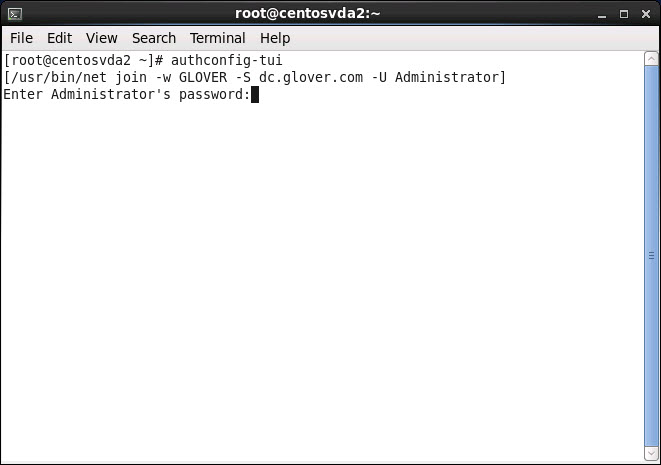
Type the Domain administrator password again in the terminal window and hit return:
Click OK:
Note: the CentOS 6.6 VM should successfully join the specified DNS Domain with the Winbind service starting:
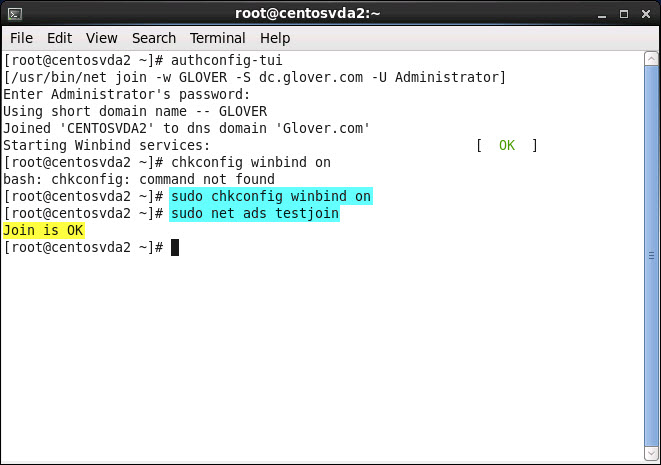
Run sudo chkconfig winbind on to ensure the winbind service starts on boot
Run sudo net ads testjoin
expected return value = Join is OK
10. Create Home Directories for Domain Users
Run the following commands in turn from within the console or terminal window
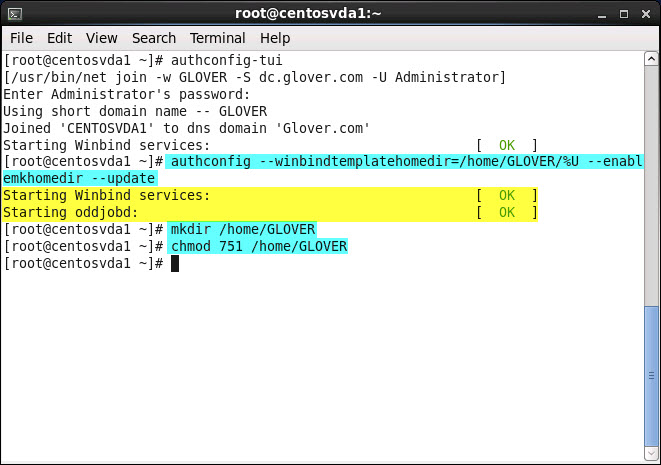
authconfig –winbindtemplatehomedir=/home/GLOVER/%U –enablemkhomedir –update
mkdir /home/GLOVER
chmod 751 /home/GLOVER
Note: Replace GLOVER with the Domain name to match your testing environment and set the appropriate permissions as per your individual requirements – Example: 751
IMPORTANT: Disable and re-enable the following option through the UI:
- Click on System > Administration > Authentication > Advanced Options and un-tick the option to “create home directories on the first login”
2. Click on System > Administration > Authentication > Advanced Options and re-tick the option to “create home directories on the first login“
Note: The above action of disabling and re-enabling home directory’s from within the UI seems to workaround what appears to be a bug when configuring Home Directory’s through the Command line.
11. Configure Kerberos for Winbind
By default, Winbind will not create the system keytab file /etc/krb5.keytab when joining the domain, which implies the Kerberos tools and libraries won’t be able to authenticate the machine account.
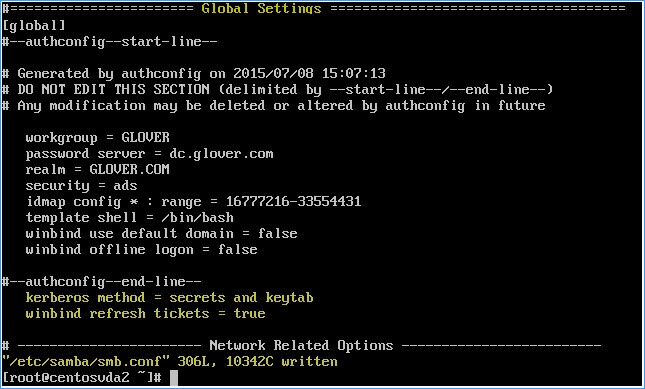
To force Winbind to create and maintain the system keytab file and automatically renew tickets, paste or type vi /etc/samba/smb.conf into the VM console window (or GUI terminal window) and hit return
– Press Shift + a to enter edit mode
– Add the following values under the Global Settings section (outside the authconfig section) of the samba configuration file:
kerberos method = secrets and keytab
winbind refresh tickets = true
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file
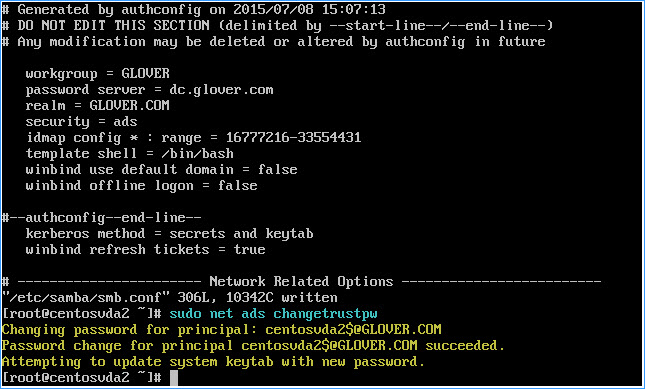
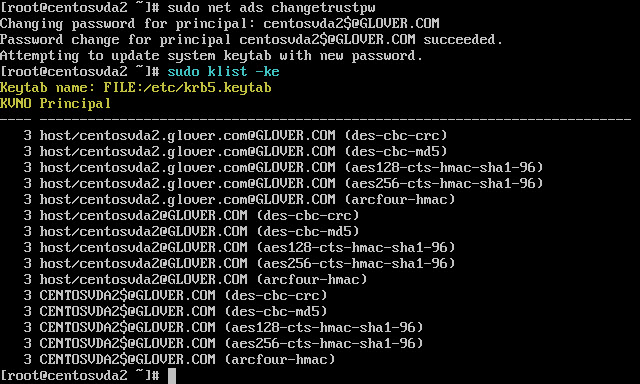
As the above settings will create the system keytab when the machine is joined to the domain (something we have already done in step 9 above), run sudo net ads changetrustpw and hit return to force the creation of the key tab file:
12. Configure PAM for Winbind
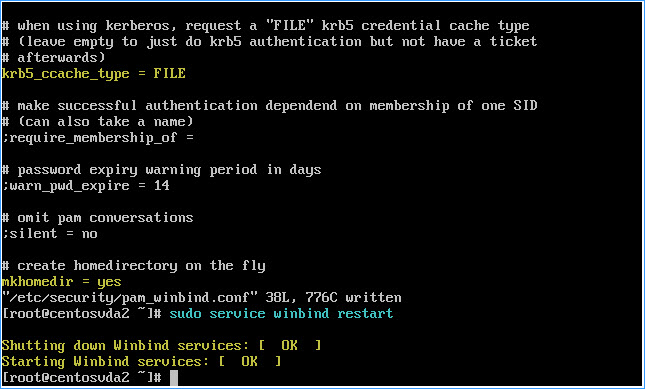
To enable Kerberos ticket caching and home directory creation for Winbind, paste or type vi /etc/security/pam_winbind.conf into the VM console window (or GUI terminal window) and hit return
– Press Shift + a to enter edit mode
– Add or change the following values under the Global section of the pam_winbind configuration file:
krb5_auth = yes
krb5_ccache_type = FILE
mkhomedir = yes
IMPORTANT: make sure to remove the semicolon preceding each of the above lines
– Press Esc
– Press Shift+z twice to exit and write changes to the configuration file
Run sudo service winbind restart to restart the Winbind daemon
Note: The winbind process will only continue to run if the machine is joined to a domain.
13. Verify Kerberos Configuration (Optional)
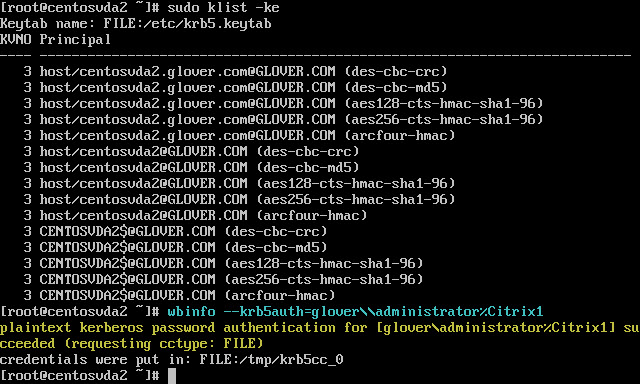
To verify Kerberos is configured correctly for use with the CentOS 6.6 VM, check that the system keytab file has been created and contains valid keys by running klist -ke at the console or terminal window:
Note: This should display the list of keys available for the various combinations of principal names and cipher suites.
14. Verify User Authentication (Optional)
Use the wbinfo tool to verify that domain users can authenticate with the domain
Run wbinfo –krb5auth=domain\\username%password
Note: The domain specified here is the AD domain name, not the Kerberos realm name. For the bash shell, the backslash (\) character must be escaped with another backslash. This command will return a message indicating success or failure.
Example: wbinfo –krb5auth=glover\\administrator%Citrix1
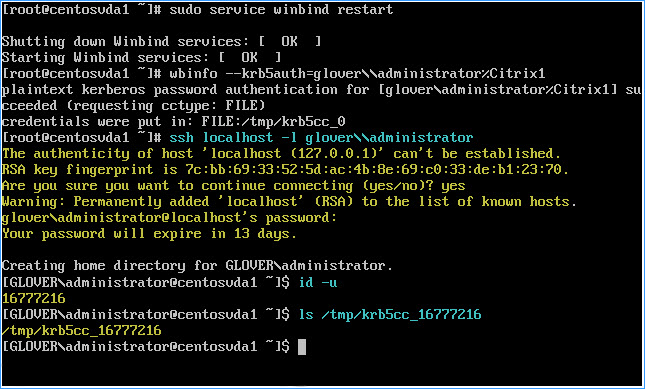
Logon locally with a domain user account that has not logged onto the machine previously to confirm that the Winbind PAM module has been configured correctly
Run ssh localhost -l domain\\username
– Example: ssh localhost -l glover\\administrator)
Run id -u
Check that a corresponding Kerberos credential cache file was created for the uid returned when running the id -u command above
Run ls /tmp/krb5cc_uid and substitute uid with the value returned when running the id -u command above
– Example: ls /tmp/krb5cc_16777216
So that’s it for now…. part 1 done and dusted. If you’ve made it this far without incident then you should take a well-earned coffee break knowing you are ready for part 2. More than likely available by the time you read this, pt.2 will cover the installation and configuration of the Linux VDA.
Follow me on @XDtipster for up to the minute BLOG release announcements including Linux VDA setup on CentOS 6.6 pt.2 (Coming VERY SOON)
Best Regards,
Mick Glover (aka XD Tipster)
Senior Readiness Specialist,
Worldwide Support Readiness [EMEA]
Citrix Systems, Inc
Follow @xdtipster