Are you, or is your company thinking about offering IoT services to its/your customers? If so, you (or they) have probably noticed that there is a lot to think about and that it goes way beyond the technology and/or tools involved. For most organisations, it requires a different mindset and a curtain degree of resourcefulness as well as creativity — not to be underestimated.
For a lot of (IT) companies the addition of the IoT to their portfolio is a big step. As part of the process a couple of questions they might be asking themselves include but are not limited to:
- What type of IoT services do we want to offer?
- Do we take on the role of IoT solutions advisor or are we better of as an integrator?
- Do we primarily focus on enterprise or consumer IoT services, or perhaps both?
- Are we, as a company able to tell our customers (or to figure out) how the IoT might be beneficial for them?
- Do we focus on one specific vertical, or multiple and why? What is our strength and the true added value we can deliver?
- While there will always be some overlap, what will be the main focus when providing these services: is it to improve overall operations, conserve resources, big data processing, adding security, increase revenue? And so on.
- Do we have any IoT architects employed already? Probably not. What about general IT administrators and/or architects who are willing and able to (re) educate themselves?
- Depending on the route taken companies might also want to consider to out-source certain tasks, like the assembly and implementation of so-called Edge sensors and/or gateways, for example.
- While answering these types of questions, make sure to involve all/any potential stakeholders within your company. This will include (in some case many) non-IT related groups and/or teams. In the end, everybody needs to be onboard regarding the company’s vision and business objectives when it comes to the IoT strategy chosen. If not, it will die an early, slow and painful dead. Remember, this is a continues process.
- The same applies to the IoT architect, or team of architects, by the way. The biggest successes come as a team effort. And are celebrated as such.
The next step
As a potential next step, it is time to think about the IoT architecture, the technology and tools involved. This will also help in determining the skills needed, technology adoption and supplier selection.
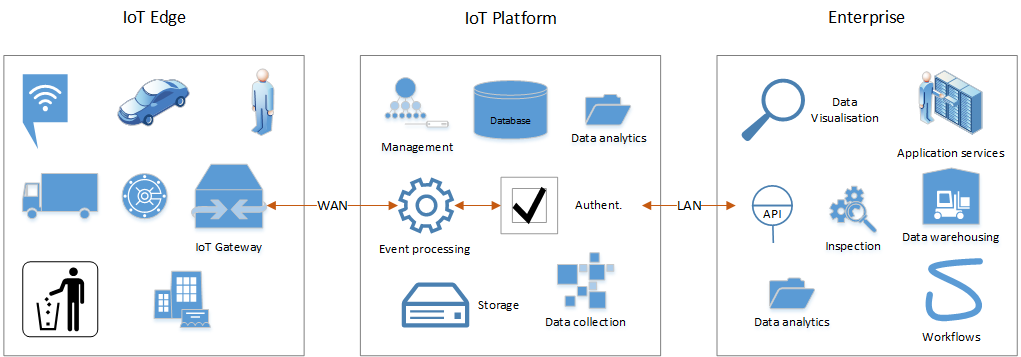
An IoT architecture roughly consists out of the following building blocks:
- The Edge.
- IoT platform.
- Enterprise
With these ‘blocks’ comes the following to keep in mind and pay attention to:
- The Edge. Meaning all sensors, gateways, including simple and smart IoT devices, and so on. Primarily hardware related.
- Big Data. This includes the understanding of how this type of technology might benefit certain companies and/or verticals as well as the soft and hardware needed to able to apply data processing and analytics (data warehousing).
- As far as the IoT platform goes, and the interaction with and between the Edge devices: authentication, event processing, the various protocols involved, the understanding and setting up of logical workflows, Edge device management, and more. Most of these items are platform agnostic. Now I wouldn’t be much of a Citrix CTP without at least mentioning the Citrix Octoblu platform, right? It can run as a SaaS offering in the Citrix cloud, as an on-premises private cloud or as an edge/mesh network in a home, car, construction site, retail store, emergency room, smart city, etc. Perhaps even better, the entire Octoblu IoT stack can run on Intel, Dell, and HPE IoT Gateways! Have a look here.
- Start evaluating various IoT platforms today, if you haven’t started already. Since IoT platforms are flexible in nature (or should be) Microsoft Azure and Amazon AWS are also two you might want to have a look at. In short, a cloud first approach when it comes to your IoT platform of choice is probably not a bad idea. As we all know, cloud services are known for their flexibility and ability to scale-up easily and quickly, which could come in handy when it comes to data analytics and things like machine learning, if you decide to take that route, that is. Since the ‘business’ questions have been answered previously, you should be able to come up with a short-list rather quickly.
- I am a firm believer in choice, I don’t believe in a one size fits all solution. I’d rather spread my options. And while this applies to IoT platforms etc. as well, I wouldn’t go and adopt more than two, let’s say max three different platforms max. IT can, or is complex as it stands today, IoT is no exception. In fact, there aren’t many IT services that potentially introduce more complexity than IoT does. There are just too many ‘things’ to consider, literally.
- When it comes to the Enterprise we are again talking about things like data warehousing, various applications services, data visualization and perhaps the most important one of them all, API integration to make most of this happen.
- Don’t worry, I won’t leave security out. Instead of listing it here I’ll address it separately.
- With all that Gartner has been putting out there, and others of course it isn’t that hard to predict that the IoT is going to be huge in the (near) future. This (2017) is the ideal time to start investing in IoT knowledge. Although you will probably outsource a couple of tasks in the process, the investment of (re) educating some of your own staff into proper IoT architects will be well worth it in the end. Don’t do like a lot did with mobile and cloud.
Though I take full credits for all the hard Visio work that has been put into this :) it’s partly based on a Gartner image I picked up earlier.
Security
IoT solutions, often tightly integrate with existing technologies and products. Needless to say that the impact of a breach or DDoS attack, to name just a few will have an even greater impact than ever before. The more ‘things’ that are and get connected the higher the risk becomes. Who would have though a couple years ago that a fridge, coffee machine or even a vent system would one day be a potential hack target? It’s funny how things change over time. In fact, this will only get worse going forward. Your security will be as strong as its weakest link, or ‘thing’ in this case. Interesting times ahead.
Breaking down the earlier mentioned IoT architecture (the three main blocks) is a good starting point when it comes to assessing and inventorying any potential security weaknesses. Let’s have a look.
- When it comes to the Edge (sensors, gateways etc.) these are components, physical in most cases that might be out of direct control of the IT department. Here you must think about things like endpoint security, the communication that takes place to and from the IoT platform (protocols, encryption etc.) and maintenance/updates cycles.
- The IoT platform, as highlighted earlier performs a lot of actions and has a lot of responsibilities. It is build up out of many components (storage, databases, analytical platforms, network, authentication mechanisms etc.). Care must be taken into securing each of these components, either physical or virtual (in software). Communication is, or should again be a big point of attention. Between the various components, the Edge devices and the Enterprise.
- The Enterprise part encompasses many components, technologies and pieces of software already known to your organization. In most cases, you will already have a though through security policy in place. Although the impact is expected to be less, it deserves the same amount of attention as all the other pieces mentioned.
- Last but not least is the human factor, which doesn’t just apply to IoT. Often security breaches are the result of an employee threating, or handling certain data in a wrong way — without any bad intentions, I might add. In some cases, it can be as simple as not opening certain emails, for example. Care must be taken into education your employees on how to threat certain data and how handle and act under certain circumstance. Security awareness, as it is called.
Rounding things up
Of course, there is a lot more that can be said/written about the Internet Of Things, but for now I’ll just leave it at this. It will be interesting to see how ‘things’ evolve going forward. Take the consumerization of IT, for example. Event though, as a company you might be focusing on Enterprise solutions when it comes to IoT, sooner or later you will have to deal with consumer devices finding, or perhaps better said, forcing their way into the enterprise. With mobility, think laptops, tablets and phones this is quite easy to imagine. But when it comes to IoT the possibilities are endless.
Thank you for reading.









One response to “Defining your IoT strategy – first things first!”
[…] Read the entire article here, Defining your IoT strategy – first things first! […]