With the introduction of Microsoft Windows 10 also came a couple of new ways to deploy and maintain Windows installations, this is what Microsoft refers to a Windows as a Service, or WaaS. Meant to make the life of the IT professional a little easier. As you might know, Windows 10 is supposed to be the final version of Windows, and thus new functionalities and features will be delivered in smaller incremental updates, two to three times per year as opposed to every 3 to 5 years prior to Windows 10, when a new version of Windows was released. This also introduces a couple of challenges when it comes to upgrading, updating and maintaining new and current installations. For this they came up with WaaS as mentioned earlier. Let’s have a look at what this means from a servicing and update perspective.
For most companies the introduction of Windows 10 also means that they will have to re-think their deployment and/or update methodology, or perhaps better formulated, strategy. To make this happen you first need to know what to take into consideration — new concepts, servicing options, tools available, the thought and philosophy behind it, never mind if you agree or not (you probably won’t get rid of Windows any time soon, so adaption is key), and so on. Only then will you be able to truly formulate a new ‘plan of attack’, so to speak. Fortunately, this will be a one-time effort, at least that’s the promise.
From a consultancy perspective the same rules apply, you will have to dig into what Microsoft has to offer before being able to successfully advise any of your customers.
Compatibility
For now, I won’t go into any of the application and/or hardware/device compatibility issues and possible remediation options available, if any. Windows 10 is supposed to be compatible with, at least, all desktop applications that also run on Windows 7 (out of the box), and when it comes to hardware compatibility they even take it one step further in stating that no new hardware will be needed since the minimum hardware requirements to run Windows 10 are the same as those needed for Windows 7. On top of that, most hardware drivers that are supported by Windows 8.1, 8 and/or Windows 7 will also continue to function under Windows 10.
However, no matter what they tell you, we all know that thoroughly testing your applications on new OS builds, including the smaller incremental Windows 10 updates mentioned earlier, is a must for all companies out there. In fact, more often than not the same will apply to security updates as well — now referred to as Quality updates as of Windows 10, but we’ll get to that in a minute.
In short, this is what Microsoft has to say about it
Windows 10 achieved such high compatibility because the changes in the existing Win32 application programming interfaces were minimal. Combined with valuable feedback via the Windows Insider Program and telemetry data, this level of compatibility can be maintained through each feature update. As for websites, Windows 10 includes Internet Explorer 11 and its backward-compatibility modes for legacy websites. Finally, Universal Windows Platform (UWP) apps follow a compatibility story similar to desktop applications, so most of them will be compatible with Windows 10
Feature and Quality updates
As mentioned, prior to Windows 10, Microsoft would release new Windows builds every few years, Windows XP, Windows 7, Windows 8, 8,1 etc. With Windows 10 future updates will be delivered more frequently, two to three times per year on average, which, by the way makes me think of another software company who recently announced a more frequent product update schedule, coincidence? A Feature update will include and provide new features and functionalities to the Windows 10 Operating System and are separate from, what they now refer to as Quality updates, which contain the well-known security fixes / patches and other non or less vital updates — does patch Tuesday ring any bells?! In short:
Feature updates: New functionalities and features. Quality updates: Security fixes / patches and other non / less-vital updates.
Tooling
The Feature updates basically replace the need for new Windows releases every few years and help in making Windows 10 more Agile, easier to test, update and implement. Even better, you can continue using the same deployment/servicing tools as you do today, which include Windows Update (although not really Enterprise worthy), SCCM, WSUS and Windows Update for Business (new).
Each of these tools offer a couple of specific configuration options when it comes to controlling and applying the various updates available. For example, depending on the version of Windows 10 (1511 or 1607 and later) in combination with your tooling of choice you will be able to postpone/defer the installation of Feature and Quality updates, varying from 30 days, up to eight months.
- SCCM – System Center Configuration Manager
- Windows Update for Business
- WSUS – Windows Server Update Services
Another thing worth noting is that with the Quality updates (security) it will now be one cumulative monthly update containing all security as well as non or less vital updates. This will ensure that all machines will be equally patched. Quality updates will be released, at least once a month (patch Tuesday), meaning that they will release any additional critical security updates when they feel it is necessary, which can be any day, any time.
Branches and Rings
To help make patching and updating easier Microsoft introduced the concepts of Servicing Branches together with so-called deployment rings.
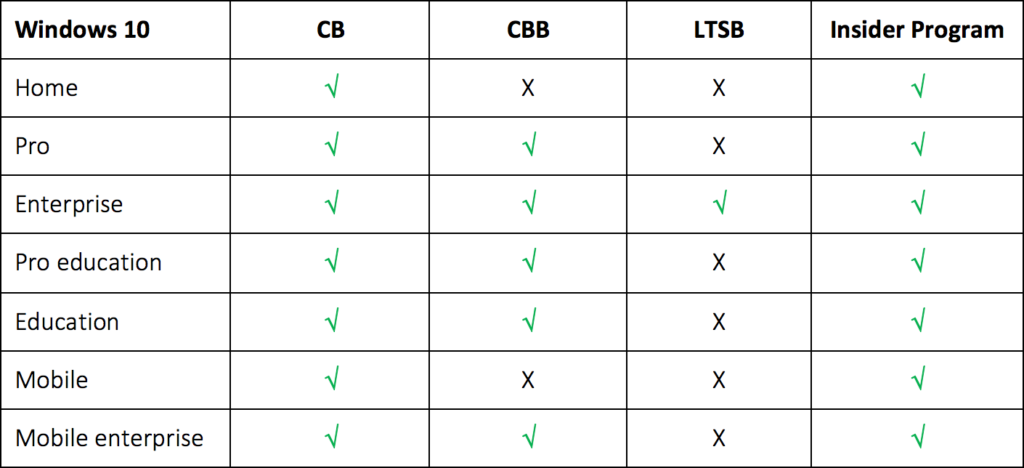
There are three different servicing branches available each offering a different approach when it comes to updating and patching your machines. The branches are: Current Branch (CB), Current Branch for Business (CBB) and Long-Term Branch (LTSB). Finally, they also have the Windows Insider program, here everyone who is interested (limited to IP professionals and partners mainly) can enter to test early prerelease Windows 10 builds and provide feedback to Microsoft.
Branches are meant for separating your devices into different (deployment) groups. This way it should become easier to control how and when you apply certain updates, this goes for both Feature as well as Quality updates.
This is also where your deployment strategy comes into play. Depending on the Branch type chosen, new updates (Feature & Quality) will either be available right away for you to deploy, they will become available after a couple of months, 4 on average, or in the case of certain specialized systems that perform a key function and are considered highly critical, you don’t want to receive or apply Feature updates at all, only Quality updates that keep them as secure as possible.
Branch types in a nutshell
Current Branch. Feature updates will be available for distribution as soon as Microsoft releases them. New updates will always be part of the CB first, making it available to any machine/member of a CB deployment group (deployment rings also play a part in this, will be discussed after Branch types) unless that machine has been specifically configured (through GPO) to defer feature updates for a certain time period. Use cases differ — developers, IT admins, PoC’s, Pilot groups, use for testing purposes etc.
Current Branch for Business. While CB will primarily be used for testing purposes, with an exception here and there, the CBB primarily focusses on company broad deployments as Microsoft likes to call it. Typically, CB releases will be transferred into the CBB after four months. Users part of the CBB will receive the exact same bits and bytes as the CB users, only at a later time. This way the software will have gone through an additional round of testing, where any issues will have been addressed by Microsoft before handing it over to the CBB deployment group.
Long-Term Servicing Branch. Last but not least. A lot of companies have machines which serve a special purpose. These are highly secure and business critical systems that, preferably do not need to be up updated with new features and/or functionalities, which could potentially ‘break’ them. This model ensures that machines that fall under the LTSB will not receive any Feature updates, only Quality updates, keeping these machines as stable and secure as possible.
As per Microsoft:
Microsoft never publishes feature updates through Windows Update on devices that run Windows 10 Enterprise LTSB. Instead, it typically offers new LTSB releases every 2–3 years, and organizations can choose to install them as in-place upgrades or even skip releases over a 10-year life cycle
Recap:
- CB: Feature updates directly available.
- CBB: Feature updates available after +- four months.
- LTSB: No Feature updates whatsoever.
- All: Quality updates available instantly.
- All: The ability to defer/postpone Feature as well as Quality updates depending on the version Windows 10 and the type of tooling used.
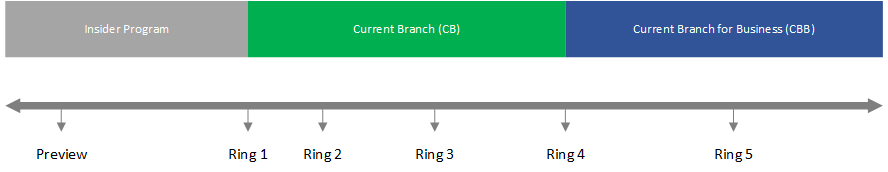
Deployment Rings
Deployment Rings are nothing more than a way to separate machines into a deployment (group) timeline. Whilst the configuration of so-called Rings slightly differs per tool, the concept remains the same. Have a look at the visual overview below, here you see the various Servicing Branches, or deployment groups, combined with multiple Deployment Rings.
A note on security/quality updates
Microsoft only talks about testing when it comes to Feature updates, but again I would like to remind you that the testing of security updates can be just as important as the testing of the incremental Features updates. While security updates are mandatory (I mean, you want your systems to be as secure as possible right?), it does help knowing if an update will break one of your applications so you can deal with it beforehand if/when possible, or at least inform your users upfront and then fix it afterwards (hopefully).
Wrapping up
There’s more to tell, there’s more for me to dive into and learn, definitely, but hopefully this does give you an idea on the direction Microsoft has taken with Windows 10, security, updates and so on. As far as a strategy goes, I will leave that up to you, at least for now.









One response to “What’s your strategy? Windows 10 Servicing Branches, Deployment Rings & tooling”
[…] Read the entire article here, Microsoft Windows 10 Servicing Branches, Deployment Rings and tooling […]