It has been a while but here is some more NetScaler madness for you, on Spilt Tunnelling this time. Hopefully I’m not boring you guys just yet (because there are a few more coming). Split tunnelling is a feature specific to SSL VPN’s and controls how the client (plugin) decides what traffic must (or may) be sent through the VPN tunnel and what traffic may be sent out directly on its local network, usually involving Internet facing traffic.
Other (related) articles from these series include:
- Citrix NetScaler Gateway, the basics!
- Citrix NetScaler (10.5) licensing. What’s new with Access Gateway!
- Citrix NetScaler… The basics continued, part one. VIP’s, Monitors and other objects!
- Citrix NetScaler… The basics continued, part two. Static routes, SNIP and MIP!
- Citrix NetScaler… The basics continued, part three. High Availability!
- Citrix NetScaler… The basics continued, Part four. What about SSL?
- Citrix NetScaler… The basics continued, Part five. Global Server Load Balancing!
- Citrix NetScaler… The basics continued, part six. Content Switching!
What it is about
Before getting into how and why Split Tunneling matters from a Citrix NetScaler perspective, here’s a global definition, or at least a part of it, which I found on Wikipedia…
Split tunneling is a computer networking concept which allows a mobile user to access dissimilar security domains like a public network (e.g., the Internet) and a local LAN or WAN at the same time, using the same or different network connections.
A bit more detail
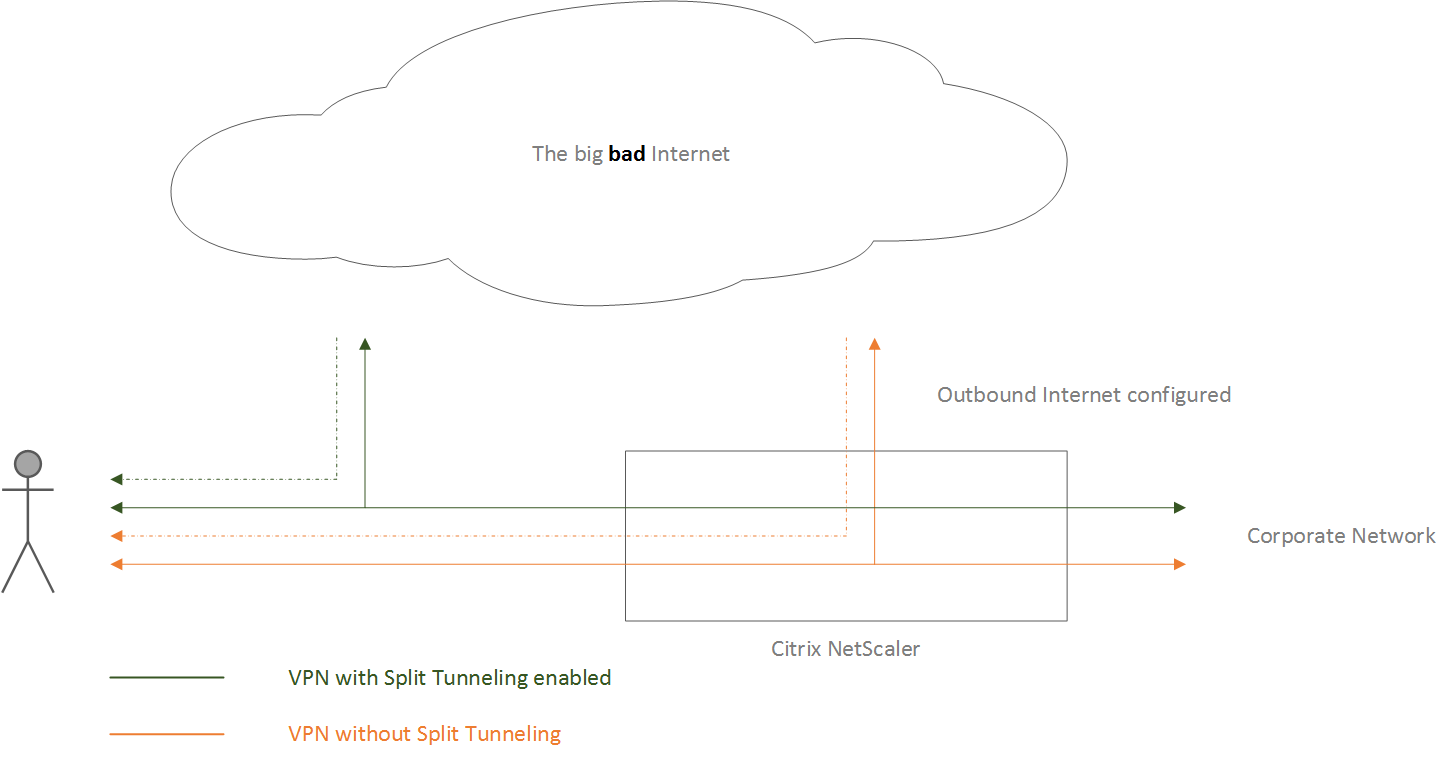
When a user connects up to the corporate network using the NetScalers SSL VPN functionality, remotely from a Starbucks café for example, we basically have two options with regards to how traffic will be routed.
First of all, we can choose to send all traffic through the NetScaler Gateway. Using this setup all traffic, including that destined for the Internet, will be send back and forth through the NetScaler Gateway to the remote connected user, assuming the NetScaler allows Internet access from the inside.
Since this might sound a bit abstract, have a look at the image below, hopefully it will clear up some questions that you might have with regards to the concept. Click to enlarge (to make it huge actually).
As a second option we can split traffic into two separate categories, Internet and VPN traffic, where traffic destined for the corporate network will be send back and forth through the NetScaler Gateway over the SSL VPN connection, while all other traffic will be send directly onto the Internet. The later is what we refer to as Split Tunneling.
Some pros and cons
When, by default, all traffic is routed through the NetScaler Gateway (over the SSL VPN) we have the ability to control and inspect all traffic up to a certain point, which can be beneficial. On the other hand, this will also ‘burden’ the NetScaler with extra load; it will simply have a lot more to do.
While in most cases this won’t to big of an issue, it’s still something to consider depending on the type and amount of traffic / data send back and forth onto the Internet. Another ‘advantage’ could be that with this setup it will be much harder to ‘grasp’ data from the outside since all traffic will be fully encrypted and inspected on an ongoing basis.
As mentioned earlier, when Split Tunneling is enabled all traffic destined for the corporate network will be send, and flow through the NetScaler gateway. All other traffic will be send out to the Internet directly from the end users computer.
This apposes a potential security threat in that when the computer of the remote logged in user get compromised, while still having an active SSL VPN connection onto the corporate network, the ‘attacker’ will have full access as well. While this may seem a bit far-fetched, it’s still something to consider and not to be taken lightly.
So how does it work?
When enabled Split Tunneling works by directly communicating (from the NetScaler) with the NetScaler Gateway Plugin (Windows or Java based) installed on the end users device. It does this on startup where it will receive a list of all so-called Intranet Applications (more on these in a minute) configured on the Gateway device.
From then on it will check all traffic originating from the remote users device by inspecting the addresses within the data packages send. It will compare them to the addresses configured in the list of Intranet Applications. If the destination address in one of the data packages matches that of one of the Intranet Applications it will be send through the Gateway. All other traffic (no match) will be discarded and send onto the Internet directly.
You basically enable split tunneling to prevent the NetScaler Gateway Plug-in from sending unnecessary network traffic to NetScaler Gateway.
So when enabled, it will prevent the plug-in from sending any non-corporate related network traffic to and through the NetScaler Gateway. If not enabled, the Gateway plug-in will capture all network traffic, including that destined for the Internet, and sends it directly through the NetScaler gateway over the SSL VPN, since no data package inspection is needed.
Intranet Applications
As mentioned, Split Tunneling is based on so-called Intranet (no, not Internet) Applications, which get configured on the NetScaler. They are configured as a NetScaler Gateway resource.
An Intranet Application is basically nothing more then a logical object representing a subnet (IP address and subnet mask), or range of subnets on the corporate network, a reference if you will. When Split Tunnelling is enabled, the addresses checked, and potentially matched in the data packages send from the user device, as mentioned above, refer to subnet addresses configured as part of an Intranet Application, or multiple.
To configure and set up Intranet Applications on the NetScaler you go to the configuration utility, then on the Configuration tab, in the navigation pane, expand NetScaler Gateway, then expand Resources and click Intranet Applications.
Once you click add you need to give it a name and choose which interception mode to configure (transparent for Windows and Proxy for the Java NetScaler Gateway Plug-in). After that you select the destination type (IP address and Netmask), select the protocol type to be used and finally you give in the IP address plus subnet mask or range of IP addresses – starting IP, ending IP etc.
Last but not least you need to configure and tell the SSL VPN to use the configured Intranet Applications. First the Split Tunneling feature needs to be enabled. When done on a global level you go to NetScaler Gateway, Global Settings, Change Global Settings, click the Client Experience tab and under ‘Split Tunneling’ select ‘On’, then click ‘Ok’. Next you select ‘Intranet Applications’, click ‘Add’ and select any of the available Intranet Applications from the list.
Finally click ‘Ok’, safe your configuration and you’re good to go.
Just on last thing
The NetScaler also supports so-called reverse Split Tunneling where all network traffic destined for any of the internal / corporate IP addresses (configured as part of the Intranet Applications) will NOT be routed through the NetScaler Gateway, the other way around. If you want to know more just check the Citrix E-Docs pages. Hopefully this clears up a thing or two around Split Tunneling. Thank you for reading.